Transparent Proxy Servers A Guide for Digital Marketers
Discover how transparent proxy servers work, why they're critical for ad verification and media buying, and how to choose the right solution for your campaigns.
A transparent proxy is a bit like an invisible toll booth on the internet. You pass right through it, your traffic gets inspected or logged, but you often have no idea it’s even there. It does its job without requiring a single tweak to your device's settings.
What Exactly Is a Transparent Proxy?
Think about the last time you connected to the Wi-Fi at an airport or coffee shop. You just connected, opened your browser, and started surfing—no manual proxy configuration needed. Behind the scenes, there was almost certainly a transparent proxy handling all your internet requests.
It's called "transparent" for a good reason: its presence is completely hidden from you. This is the key thing that sets it apart from a standard proxy. With a regular (or "explicit") proxy, you have to go into your browser or app settings and manually type in the proxy's IP address and port number. A transparent proxy, on the other hand, intercepts your traffic automatically at the network level.
How Does It Work Without You Knowing?
The secret lies in the network's infrastructure, usually the router or gateway. When you send a request—say, to open a website—the network hardware doesn't send it straight to the internet. Instead, it’s been pre-configured to hijack all web traffic (typically HTTP and HTTPS) and reroute it through the proxy server first.
The proxy then takes your request, sends it out to the destination server on your behalf, gets the response, and passes it back to you. The whole process is mandatory. You can't just turn it off, because the redirection rule isn't on your computer; it's baked into the network you're using. This setup gives network administrators a powerful way to manage internet access for everyone connected.
Think of a transparent proxy as an unavoidable security checkpoint in an office building. You don't get to choose whether to go through it; the building's layout forces everyone to pass security before they can get to the elevators.
What Are They Used For?
Organizations don't set these up just for fun. Transparent proxies serve some very specific and practical purposes that rely on their ability to control traffic without needing anyone's cooperation.
Here are the most common uses:
- Content Filtering: This is a big one for schools and corporate offices. They use transparent proxies to block social media, adult content, or any other sites that violate their usage policies. It's an easy way to enforce the rules for everyone.
- Security Scans: By funneling all traffic through one point, they can scan for malware, block known phishing sites, and provide a basic layer of defense for every single device on the network.
- Saving Bandwidth: They often cache popular content. If one person on the network watches a viral video, the proxy saves a copy. When the next person wants to watch it, the proxy delivers it from its local cache instead of downloading it again, which saves bandwidth and makes things feel faster.
- Forcing Logins: Those "captive portals" on public Wi-Fi networks that make you agree to terms or enter a password? That's usually a transparent proxy at work, redirecting your first request to a login page.
Now that we've got the basics down, it's time to dig deeper. While this seamless control is great for network admins, the invisible nature of transparent proxies raises some serious questions about privacy and security, which we'll get into next.
How Transparent Proxies Technically Work
To really get what makes transparent proxies tick—and understand their risks—we need to pop the hood and see how they actually handle your data. Unlike a proxy you’d set up yourself, a transparent proxy works quietly in the background at the network level, intercepting everything without your device even knowing it's there.
Think of it like a security checkpoint at an office building's exit. Every person leaving is automatically routed through it. The guard doesn't change where you're going, but they might check your badge and log your departure time before letting you pass. A transparent proxy does the same thing for your internet traffic.
This diagram lays out the basic journey your data takes when a transparent proxy is on the job.
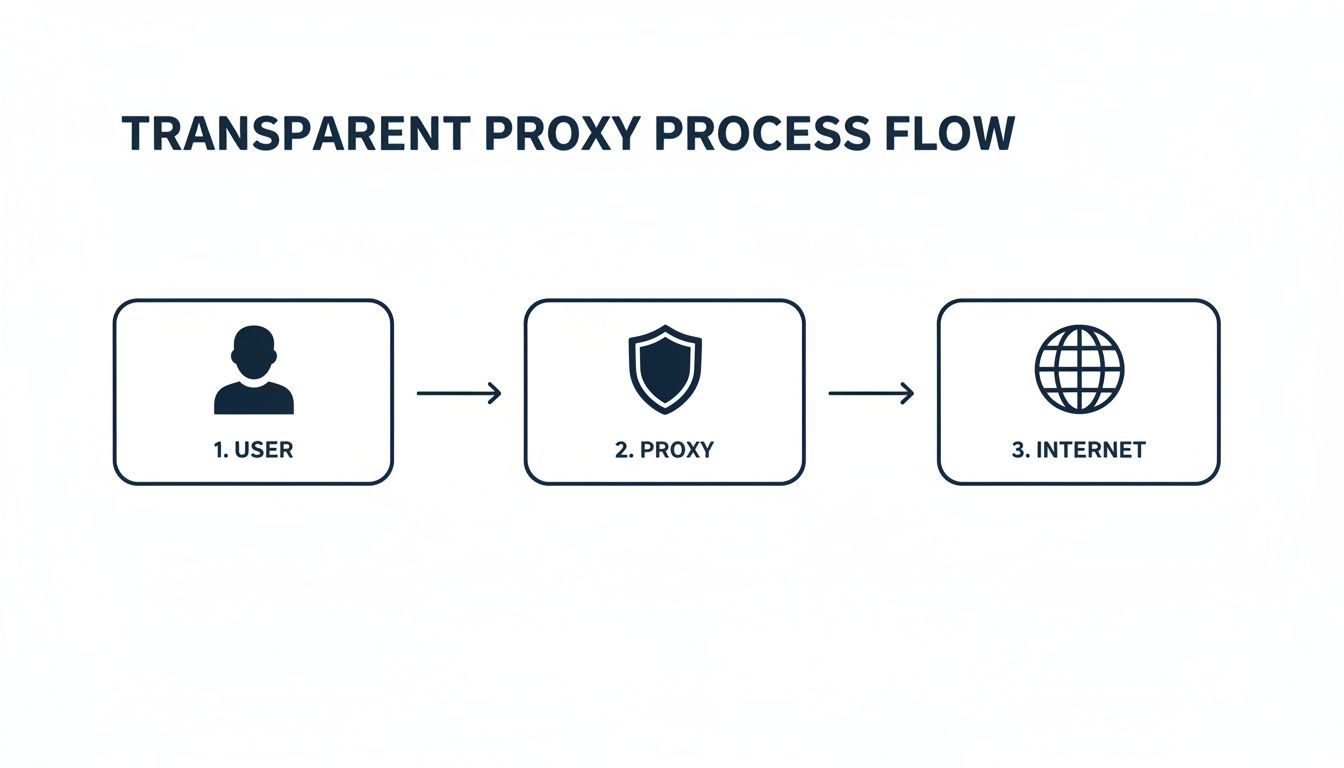
As you can see, the flow is straightforward but powerful. Your request gets seamlessly rerouted through the proxy before it hits the open internet, and your device is none the wiser.
Intercepting Traffic at the Source
The real magic is in the network redirection. When you try to visit a website, your request is essentially hijacked by a router or firewall on the network.
Instead of sending your traffic straight out to the internet, the hardware shunts it over to the transparent proxy server first. This isn't optional; it's a mandatory detour enforced by the network administrator. Your computer or phone thinks it's talking directly to the website, but it’s really having a conversation with the proxy all along.
The Role of HTTP Headers and IP Passthrough
Now we get to the technical bits that are crucial for privacy and data analysis. When the transparent proxy grabs your request, it sends it on to the final destination, but it usually tacks on a few extra HTTP headers. These headers give the destination server some important context.
The most famous of these is the X-Forwarded-For header. This little piece of data contains your original IP address. It’s the proxy’s way of telling the server, "Hey, this request is coming from me, but it was originally sent by this specific user."
This IP "passthrough" is the defining feature of a transparent proxy. While it manages the traffic, it makes zero effort to hide who you are. This is exactly why "transparent" does not mean "anonymous."
This total visibility is a double-edged sword. For a network admin, it provides the traceability they need to monitor and secure the network. But for a user, it means their real IP address is completely exposed to every website they visit, offering no privacy at all.
How Transparency Compares to Other Proxy Types
It's vital to understand that not all proxies are created equal, especially when it comes to handling your IP address. A transparent proxy is just one piece of a much larger puzzle.
To put it in perspective, let's compare how different proxies manage your identity online. This table breaks down the key distinctions between transparent, anonymous, and elite proxies, showing how they handle your IP and the headers that can give you away.
Proxy Type Comparison: How They Handle Your IP and Headers
| Proxy Type | Original IP Visibility | HTTP Header Modification | Primary Use Case |
|---|---|---|---|
| Transparent | Visible via X-Forwarded-For | Adds headers revealing the original IP | Content filtering, caching, network security |
| Anonymous | Hidden from the server | Modifies headers but still identifies itself as a proxy | Basic privacy, getting around geo-blocks |
| Elite | Completely Hidden | Removes all headers that identify it as a proxy | Maximum anonymity, advanced web scraping |
As the table shows, the right tool depends entirely on the job. A transparent proxy is perfect for managing an internal network where you want visibility. But for tasks like media buying or ad verification, where getting caught can ruin your data, you need a far more discreet approach.
The use of transparent proxies has exploded as companies grapple with cybersecurity threats and complex data privacy laws. Over 4.2 billion internet users have had their content mediated by a proxy, with 1.1 billion instances of data masking involved. Transparent proxies are great for enforcing company-wide policies silently, which is crucial for ad verification teams trying to confirm brand safety across 195+ countries—especially when geo-targeting fails 28% of the time due to unfiltered IPs. You can explore additional proxy market insights here to see just how widespread this technology has become.
Why the Right Proxy Is a Game-Changer in Media Buying
In digital advertising, accuracy isn't just a goal; it's everything. Media buyers and ad verification teams are in a constant battle to make sure their campaigns hit the right audience, in the right place, and next to brand-safe content. This is where proxies come in—they're an essential tool of the trade. But here's the catch: not all proxies are created equal.
Let's say you're running a campaign targeting users only in Tokyo. How do you know your ads are actually showing up there? You need to see what a user in Tokyo sees. The standard way to do this is with a proxy, which lets you check ad placements and competitor campaigns from a Tokyo-based IP address, all without leaving your desk.
This is where things get tricky. Ad networks and major platforms have gotten incredibly good at sniffing out and blocking traffic from cheap, low-quality proxies—especially those coming from data centers. The moment a platform flags your IP as a proxy, it’s game over. Your data is invalidated, your connection gets blocked, and your entire campaign could even be penalized. The result? Wasted ad spend and analytics that are completely off.
Your IP's "Trust Score" Is Non-Negotiable
Every IP address has a reputation, or a "trust score." IPs from data centers or known proxy farms have terrible scores because they're magnets for bots and fraud. For a media buyer, using one of these IPs is like sending a spy with a neon sign into a high-security building. They get spotted and shut down immediately.
This is exactly why understanding transparent proxy servers is so critical, especially when you pair them with high-quality residential IPs. A well-managed proxy service gives you access to clean, ethically sourced residential IPs—the same kind real people use in their homes. This lets your verification traffic blend in with the crowd, keeping your trust score high and your operations under the radar.
The whole point is to look like a genuine user from a specific location. If your proxy is easily detected, it defeats the purpose of ad verification, pollutes your data, and can get your accounts restricted.
Transparent proxy servers are the fastest-growing segment in the proxy server service market for a reason: they offer seamless integration and solid security. For media buying agencies, this means more reliable ad verification, even at a massive scale. It's no surprise, given that IP blocks on platforms like Google Ads and Meta have jumped 35% in the last year due to suspicious traffic.
Preventing IP Leaks That Can Wreck Your Campaigns
Even with a top-notch residential IP, a simple data leak can compromise everything. As we've covered, transparent proxies can pass your original IP address in headers like X-Forwarded-For. If your proxy service isn't built to handle this, the leak will expose your real location and instantly discredit your verification efforts.
This is a problem a professional solution like ProxyPurpose is built to solve. It uses an advanced architecture designed to stop these leaks and keep your campaign data safe. Here’s how it tackles the biggest challenges for media buyers:
- Clean Residential IPs: You get access to a pool of dedicated, constantly monitored residential IPs with high trust scores, so you can verify ads without getting blocked.
- Leak Protection: Features like Shield Protection actively prevent DNS leaks and other ways your data could be exposed, making sure your real IP and location stay hidden.
- Smart Routing: Traffic is intelligently routed through the fastest and most reliable global paths, cutting down on lag and keeping your verification tools running smoothly.
By combining the principles of transparent proxying with a secure, robust infrastructure, media buyers can finally get the accuracy they need to run successful global campaigns. It eliminates the risk of burning money on blocked IPs and ensures the data you rely on is clean, accurate, and trustworthy.
Security Benefits vs. Privacy Risks: A Double-Edged Sword
Transparent proxies walk a fine line, acting as both a powerful security tool and a potential privacy weak point. For anyone managing a network, their value is obvious. They give you a single point of control over all traffic leaving your network, creating a solid first line of defense that works without anyone having to lift a finger.
This centralized approach lets organizations apply security rules across the board. A transparent proxy can instantly shut down access to known malicious sites, filter out unwanted content, and even scan for viruses before they have a chance to infect a user's computer. Think of it as a mandatory security checkpoint that every piece of data has to pass through.
The Upside: Centralized Control and a Stronger Defense
For any organization, from a small business to a massive corporation, the benefits of this forced interception are huge. By funneling all traffic through one choke point, network administrators get a bird's-eye view of everything happening and can enforce policies with surgical precision.
- Content Filtering: This is a classic use case. Schools use them to keep students on task by blocking social media, and companies use them to enforce acceptable use policies.
- Malware Protection: They can stop users from wandering onto phishing sites or downloading malware by cross-referencing requests with real-time threat databases.
- Bandwidth Management: By caching frequently accessed websites and files, they take a huge load off the network, which means faster browsing for everyone and lower bandwidth costs.
This kind of setup is becoming more and more crucial. In large-scale data gathering and ad operations, transparent proxies are key for ensuring compliance and performance, especially in highly regulated markets. The numbers tell the story: 60% of small businesses and enterprises are now using cloud-based proxy deployments. Plus, when you add in modern features like AI-powered threat detection, companies have seen security breaches drop by as much as 42% in industries like retail. You can find more detailed stats on the proxy server market over at MarketResearchIntellect.com.
The Downside: Who's Watching the Watcher?
Here's the catch. The very same mechanism that provides all that security also creates some serious privacy headaches. Since a transparent proxy sits right in the middle of your connection, it can potentially see everything you do online—especially if your traffic isn't encrypted (plain old HTTP).
This opens the door to a huge risk if the proxy is run by someone you can't trust or if it gets hacked. A bad actor who gains control of a transparent proxy could launch a man-in-the-middle (MITM) attack, allowing them to read, change, or steal sensitive information like your login details or financial data as it flies by.
It's vital to remember this: 'transparent' is the exact opposite of 'anonymous.' A transparent proxy is built for visibility and control from the admin's side, not to hide who you are. It dutifully passes your real IP address right along to the final destination.
This is why the integrity of the person or company running the proxy is everything. When you hop on the public Wi-Fi at a coffee shop or airport, you're trusting them to run their transparent proxy securely and ethically. For critical business activities like ad verification or scraping data, you can't afford to take that chance. Using a professional proxy service that puts security first isn't just a good idea—it's absolutely essential to protect your operations.
How to Spot and Handle Proxy Risks
Because transparent proxies are built to be invisible, finding them takes a little detective work. The good news is, a few simple checks can tell you if your connection is being intercepted, which is the first step toward protecting your data and your business.
The quickest way to check for a proxy is to use an online IP detection tool. These websites look at the HTTP headers your browser sends. If they spot headers like X-Forwarded-For or Via, that's a dead giveaway your traffic is passing through an intermediary server.
These headers are breadcrumbs left by the proxy to provide info about the original request, basically announcing its own presence. For any user, this is the most direct way to get a quick snapshot of their connection's path.
Practical Ways Businesses Can Mitigate Risk
If you find a transparent proxy on a network you don’t manage—think public Wi-Fi—it should immediately set off security alarms. That proxy can see any unencrypted traffic, so protecting your sensitive data has to be your number one priority. Your most powerful weapon here is end-to-end encryption.
By making sure all your traffic is wrapped in HTTPS (Hypertext Transfer Protocol Secure), you create a private, encrypted tunnel between your device and the server you're connecting to. The proxy might see which domain you're visiting, but it won't be able to decipher the actual data flowing back and forth.
Key Takeaway: Encryption is your best defense. A transparent proxy can't read what it can't decrypt, making HTTPS an absolute must-have for securing data on any network.
But for businesses involved in critical tasks like ad verification or scraping data at scale, just using HTTPS is not enough. Professional-grade operations need stronger security to stop data leaks that could wreck a campaign or expose your company's real IP addresses.
Advanced Protection to Plug Data Leaks
Even with HTTPS enabled, other weak points like DNS leaks can still expose what you're doing online. A DNS leak happens when your requests to find a website's IP address are sent over an unsecured channel, revealing every site you visit to the network owner or anyone else listening in.
This is where you need to bring in a specialized proxy solution. A high-quality service built for business use will have features designed specifically to close these security holes. For instance, a dedicated solution can:
- Block DNS Leaks: This forces all your DNS requests through the secure proxy network, so nothing leaks out through unencrypted channels.
- Prevent Fingerprinting: It can actively block scripts that websites use to identify and track your device, adding a crucial layer of operational security.
- Guarantee Clean IPs: You get access to a pool of high-reputation residential IPs that haven’t been flagged by ad platforms, making sure your ad verification is both accurate and under the radar.
For data engineers and media buyers, these aren't just nice-to-haves; they're essential. Using a service like ProxyPurpose and its Shield Protection feature ensures your work stays completely confidential and effective. It turns a potentially risky network into a secure, controlled environment, letting you get the job done with total confidence.
Choosing the Right Proxy for Your Business Needs
<iframe width="100%" style="aspect-ratio: 16 / 9;" src="https://www.youtube.com/embed/j9-Y0KWVJ1k" frameborder="0" allow="autoplay; encrypted-media" allowfullscreen></iframe>Diving into the world of proxies can feel overwhelming, but it really boils down to this: each proxy type is a tool built for a specific job. Transparent, anonymous, and reverse proxies all solve different problems, and picking the right one is absolutely critical for success, especially in high-stakes industries like media buying and ad verification.
Let's break it down with an analogy. A transparent proxy is like a security checkpoint at a company's front gate—it manages traffic for safety and efficiency but doesn't hide anyone's identity. An anonymous proxy, on the other hand, is like a disguise, masking your real IP address to give you privacy. Finally, a reverse proxy acts more like a bodyguard for a server, fielding all incoming requests to boost performance and security. For complex tasks that demand both privacy and high performance, none of these options really work on their own.
Beyond Basic Proxies for Demanding Use Cases
When your day-to-day involves verifying millions of ad impressions or scraping massive amounts of market data, the risks of using the wrong tool are huge. Ad platforms have become incredibly sophisticated at sniffing out and blocking IPs from generic data centers or shady proxy networks. Just one flagged IP can tank your data's credibility, burn through thousands in ad spend, and even get your accounts shut down.
This is where you move past off-the-shelf proxies and into a professional, purpose-built service. You don't just need a generic tool; you need an integrated solution designed to tackle the real-world challenges of modern digital operations.
For media buyers and data teams, the goal isn't just to use a proxy—it's to appear as a legitimate, high-trust user from a specific location. Success depends on a proxy infrastructure that is undetectable, fast, and secure by design.
The Professional Solution for Performance and Accuracy
A service like ProxyPurpose was created to solve these exact problems. It blends the best features of different proxy concepts into one powerful platform, specifically for performance-critical work. Here’s where it makes a real difference:
- Clean Residential IPs: You get access to a dedicated pool of high-reputation residential IPs. These are constantly checked to make sure they're clean and not on any blocklists, so you can verify campaigns and gather data without worrying about getting shut down.
- Smart Global Routing: An intelligent routing system automatically figures out the fastest and most reliable path for your traffic. This slashes latency and keeps your tools running at peak speed, which is a must-have for any time-sensitive data collection.
- Advanced Security with Shield Protection: Features like Shield Protection add another layer of defense by actively preventing DNS leaks and other ways your real data could be exposed. It ensures your true location stays private and your operational security is never at risk.
By investing in a solution built for the job, you can stop wasting ad spend, achieve incredible campaign accuracy, and grow your operations with confidence. It’s time to graduate from basic proxies and start using a tool engineered for your success.
Frequently Asked Questions
Got more questions? You're not alone. Let's dive into some of the most common things people ask about transparent proxies to clear up any lingering confusion.
Can a VPN Get Around a Transparent Proxy?
Yes, in most cases, a VPN is a great way to bypass a transparent proxy. When you connect to a VPN, it wraps all your internet traffic in an encrypted tunnel. From the proxy's perspective, all it sees is a single, scrambled connection to a VPN server—it has no idea what websites you're actually visiting, making its filtering rules completely ineffective.
Keep in mind, though, that some sophisticated networks deploy advanced firewalls specifically designed to spot and block VPN traffic. For something as crucial as ad verification or secure media buying, a dedicated proxy service is a far more reliable tool than a general-purpose VPN.
Is a Transparent Proxy Just Another Name for a Forward Proxy?
That's a good way to think about it. A transparent proxy is a type of forward proxy. The term "forward proxy" is just a catch-all for any server that acts as a middleman between a user's device and the internet, forwarding requests for them.
The real difference comes down to how you connect to it. A regular, or "explicit," forward proxy needs you to go into your browser or device settings and manually configure it. A transparent proxy, on the other hand, is set up on the network itself. It grabs your traffic automatically without you having to do anything, making it totally invisible to you as the user.
The bottom line is this: transparent proxies are mandatory and invisible, while standard forward proxies are optional and require you to set them up.
Are Transparent Proxies Any Good for Web Scraping?
Not if you're using a basic, standard one. A typical transparent proxy is actually terrible for web scraping because it forwards your real IP address in the request headers for everyone to see. That’s a surefire way to get blocked.
However, the technology behind it can be incredibly powerful when used correctly. A professional proxy provider can leverage this infrastructure to manage a huge pool of clean, rotating residential IPs. This allows you to run massive scraping projects efficiently, rotating through trusted IPs to avoid getting rate-limited or banned. You get all the benefits without the nightmare of managing the proxies yourself.
Is It Legal to Use a Transparent Proxy?
Yes, absolutely. Using transparent proxies is a perfectly legal and common practice for managing networks. You’ll find them used by corporations, internet service providers (ISPs), and even your local coffee shop's public Wi-Fi. They use them for totally legitimate reasons, like filtering harmful content, beefing up security, or caching data to speed things up.
As with any tool, the legality comes down to how you use it, not the technology itself. When you're using a trusted proxy service for business tasks like ad verification, market research, or media buying, you're on solid ground. Reputable providers ensure their IPs are ethically sourced, keeping your operations fully compliant and above board.
Ready to stop wasting ad spend and get the real story behind your campaign performance? ProxyPurpose Inc. delivers the clean, high-trust residential IPs and rock-solid infrastructure you need to operate with total confidence. Find out how ProxyPurpose can sharpen your operations today.